Deliverability
What is DMARC and how does it work

Deliverability

Mailbox providers have gotten pretty good at spotting – and eliminating – dangerous, unwanted emails. But some spam still gets through. These messages have the potential to do damage to both individuals and companies.
That’s why email authentication has continued to grow in importance, DMARC included. In February 2024, both Yahoo and Google updated their policies requiring that bulk email senders begin using DMARC to authenticate their emails.
These new requirements go quite a bit further than anything we’ve seen, and it’s very possible that they’ll take it even further once these are adopted by enough email senders.
In other words, if your company does any amount of consistent email marketing, you want to get ahead of this, not ignore it. Because if your emails fail validation, they won’t get delivered. And an undelivered email has a pretty tough time making any money.
Domain-based Message Authentication Reporting and Conformance (DMARC) is an email authentication system created to protect your domain from being used for email spoofing, phishing scams, and other cybercrimes. It was created as an email security protocol in 2012 by PayPal with help from Google, Microsoft, and Yahoo.
The idea is to tell mailbox providers what to do with any emails that fail authentication. Currently, there are two primary email authentication techniques: SPF (sender policy framework) and DKIM (domain keys identified mail).
But if an email fails either SPF or DKIM authentication, what happens? Well, without a DMARC policy, it kind of depends on what the mailbox provider decides to do. They can let those emails pass through to the inbox, they can filter them out as spam, or they can prevent them from being delivered.
When a domain owner sets up a DMARC record in their DNS, they can request insights into who is sending emails on behalf of their domain.
A DMARC record is a basically a line of code that is added to your DNS TXT record, with important information regarding what to do when this authentication fails:
As mentioned, DMARC uses SPF and DKIM to authenticate the messages and tells the mailbox provider what to do with incoming emails that fail these email authentication protocols.
This means no one will be able to spoof your email domain– that is, borrow it to send an email asking for a $100 donation for the Amazon rainforest, and then use the money to buy a new yacht…to go see the Amazon rainforest.
With a DMARC policy in place, you and your subscribers all benefit. Here’s what happens once you set up DMARC:
Email marketing begins with deliverability and protecting your sender reputation is key. As mailbox providers ramp up their efforts to stamp out spam and email fraud, more emails will get rejected. Without a DMARC policy in place, senders run the risk of having more of their emails rejected, which will significantly impact their revenue.
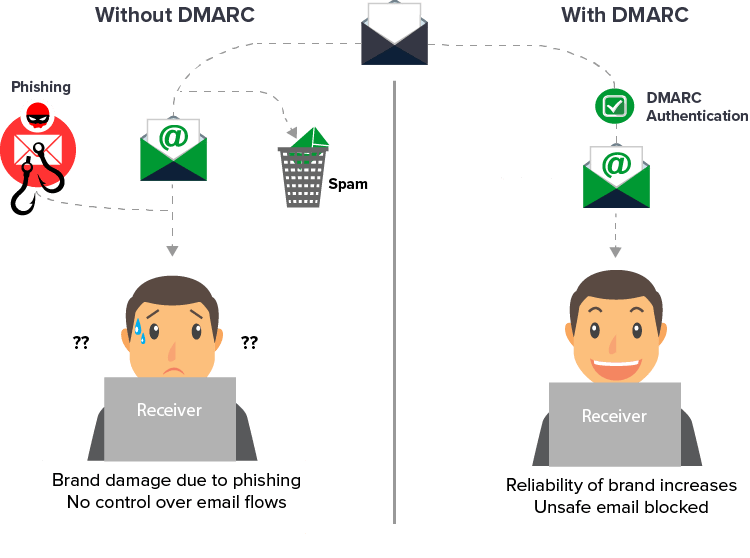
But it’s not just about deliverability. When scammers use your domain to try to defraud people, it severely damages your brand’s reputation, and makes it harder for people to trust your legitimate emails – even if it’s not your fault.
Using DMARC will make it much harder for scammers to spoof your domain, and adding BIMI as an extra layer of authentication will help strengthen trust with your audience.
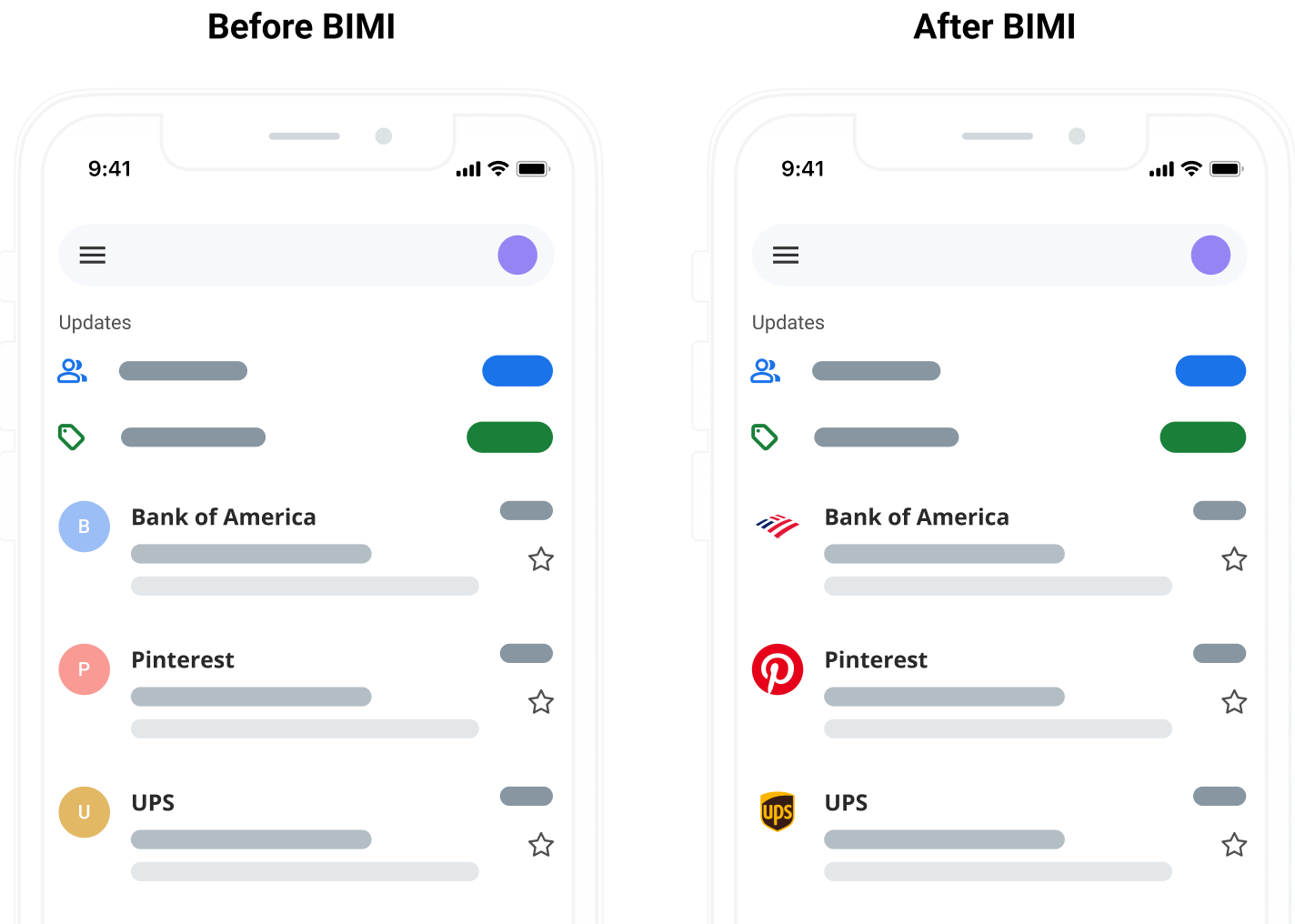
With BIMI, the sender can put their logo right next to the subject line, confirming to the recipient that they are the sender. This is not something a scammer can duplicate. Why not? Because the only way to use BIMI is to have a working DMARC policy.
You cannot utilize DMARC until you implement SPF and DKIM, both of which are set up in your DNS. Once those are in place, you can use DMARC to tell mailbox providers what to do if an email fails either of these policies.
In short, SPF and DKIM are both email authentication methods that inform mailbox providers that an email comes from a legitimate sender:
But what happens next? If an email fails either SPF or DKIM, your DMARC policy will answer that question.
You can set your DMARC policy to one of three settings, which will indicate what needs to happen with these emails that have failed SPF or DKIM.
Here’s each setting and what they mean:
Every major mailbox provider performs a DMARC check, so having DMARC set up will offer additional protection with all the main email clients.
Further survey results from our Road to the Inbox: Navigating email deliverability in 2025 indicate that cuurently, the p=none policy is the most used at nearly 32%. That’s followed by more than 19% who use p=quarantine and 17.5% who use p=reject. More than 31% of senders who use DMARC are unsure what their policy is.
While the new sender requirements only dictate that senders use a policy of None, that is expected to change. Google and Yahoo made it easy for now because their goal was to increase DMARC adoption. Representatives from these mailbox providers have said that they ultimately want more organizations to enforce DMARC with a p=reject policy.
Deliverability experts agree. Sticking with a p=none policy means you’re not getting the most out of DMARC. Unfortunately, many senders in our survey said they’d only update their DMARC policy if it was required.
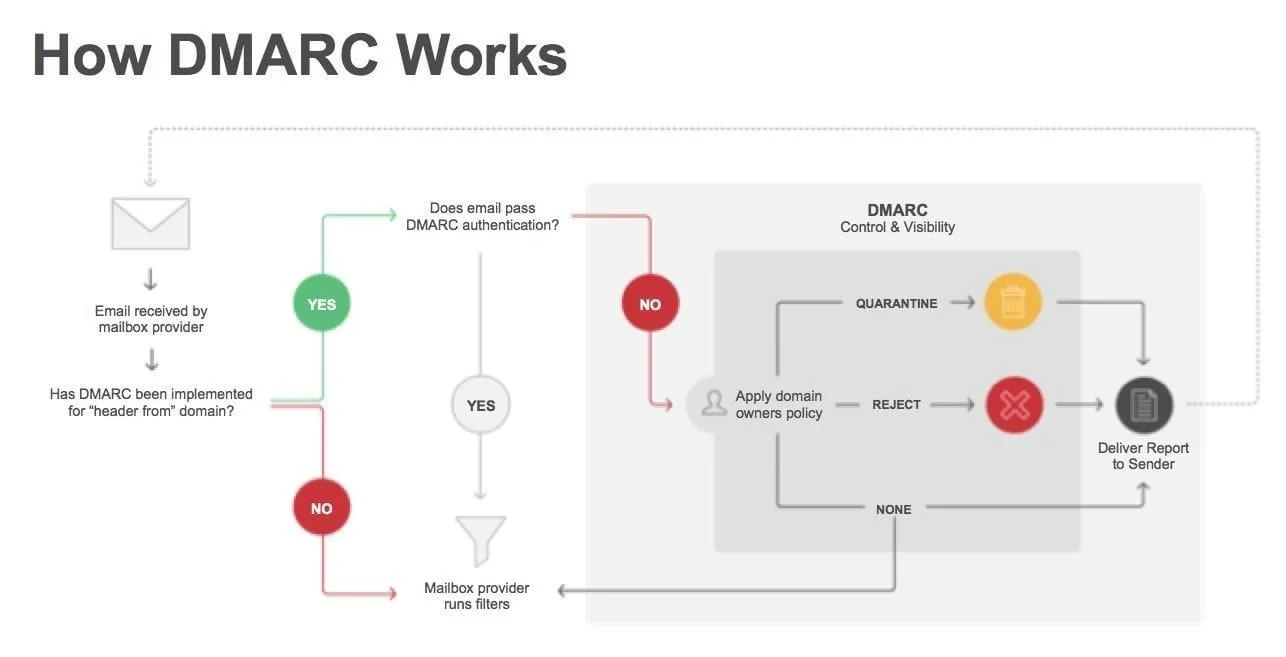
Let’s get into the details a bit more and go through the steps of how DMARC validates incoming emails:
With this email authentication process, no one will be able to spoof your email domain and expect their fraudulent emails to make it to anyone’s inbox, because their emails will fail these tests.
I think using p=none is a great start. Baby steps. But it doesn’t ever have any teeth if you aren’t upping that to another level. And that’s the main purpose of DMARC – to not allow others to send as you.
A DMARC report is a document that contains all the key information about the authenticity status and email traffic sent on behalf of a domain. This includes how many emails passed DMARC evaluation, their source IP address, and how many were sent in total.
There are two types of DMARC reports you can get: aggregated and forensic. These reports help ensure that you are properly authenticating your outbound emails.
Here’s a quick look at each.
These daily reports are XML documents, and they present data about any emails that claimed to be from one of your domains or subdomains. Those reports are meant to be machine-readable.
With aggregate reports, you’ll get a broad look at how often emails claiming to be sent from your domain are failing authentication.
While aggregate reports give a solid overview, its the forensic reports that get into the nitty gritty.
Here, you’ll see individual copies of the actual emails that failed authentication, along with other data, enclosed in a full email message to the address you specify in your DMARC record.
Unlike with aggregate reports, people can easily read forensic reports. You’ll see information such as:
Looking to set up DMARC? Then follow this quick, easy-to-follow 5-step process:
Setting up SPF and DKIM is the first thing you’ll need to consider if you want to implement DMARC. If you’ve already done this, you can skip to Step 2.
If you haven’t, you’ll have to get into your DNS settings, which you can find through your hosting plan or domain name provider.
To set up SPF and DKIM, you must add DNS TXT records from your email service provider and paste it into your DNS at the appropriate place. Every host will have a slightly different procedure for this, so you can either contact their customer support, use your existing knowledge, or do a web search for ‘how to set up SPF in [hostname].’
As mentioned earlier, you’ll want a unique business email address to receive the XML aggregate reports and the forensic reports. There are third-party services that can help with this.
If you plan to set up DMARC for multiple domains, you may need more than one email address. You’ll input these email addresses using the rua and ruf tags in your DMARC record, as explained in our post “Breaking down a DMARC record”.
This is also a good time to prepare a list of all your sending domains and IP addresses so you can easily confirm whether the domains showing up in your DMARC reports are fraudulent, or if they are coming from you but are for some reason failing to pass authentication.
This is again why you want to set your initial policy to p=none – in case your real emails are failing.
Next, decide whether you want to go with none, quarantine, or reject for your DMARC policy, as well as a percentage of emails that policy will apply to if you want to start off with something less than 100%. If your company is large, it would be wise to start off smaller.
It’s also important to note here that if you plan to utilize BIMI, the subject-line-adjacent logo we discussed earlier, your DMARC policy cannot be set to none. So, you’ll want to establish your DMARC efforts before setting up BIMI.
Once you’ve created your DMARC policy, you can go to your host’s DNS settings and publish it.
Here’s the basic procedure:
Is it really that simple?
Well, yes and no. Once you know what you want to do, it’s relatively easy – but implementation is only the first part.
As your DMARC reports begin arriving at the email addresses you specified, start analyzing the data and preparing your response.
Once you analyze your data, you’ll be able to make decisions about these and other aspects of DMARC policy.
For example, if your data reveals that several of your legitimate emails are failing authentication, that’s something you’d want to address before changing your DMARC policy from p=none to something else. What this may mean is that you need to add DMARC records to other IPs and other sending domains you may have missed the first time around.
Learn more about DMARC from experts Ash Morin from Dmarcian and Kate Nowrouzi, VP of Deliverability at Sinch Mailgun, on Sinch Mailgun’s podcast, Email’s Not Dead.
We understand that’s a lot of information to go through in one day, and sometimes, it’s difficult to take it all in. So, you might be wondering, what should your first DMARC record look like?
We recommend something like this:
v=DMARC1;p=none;pct=100;rua=mailto:postmaster@dmarcdomain.com
Start off with p=none, because you want to see your data first. And use 100 for the percentage because you want to see all the data, and there’s no reason to set it for anything else with a p=none value.
Once you’re ready to start quarantining, change the p value, and reduce the percentage down by 5 or 10. Gradually increase it until you reach 100% and are confident that all quarantined messages are being correctly identified.
Then, change the p value again, to reject, and take the percentage back down by 5 or 10, and go through the same process. Ultimately, you’ll be able to apply stricter settings with very minimal risk.
That’s a great question, and probably one you asked yourself before clicking through to this article.
In short, if your company sends emails with personal information (invoices, order confirmations, account activation) or for marketing purposes, you need to implement one or more forms of email authentication.
This is the only way for mailbox providers to verify that an email claiming to be from you actually comes from your sending domain. And if you’re sending more than 5000 emails per day, getting your DMARC policy in place is especially urgent, or else Yahoo and Google will begin clamping down on your emails.
But even if you’re not currently classified as a ‘bulk sender’ and are under the 5000-email threshold, you shouldn’t assume it will stay that way.
That’s why, even though DMARC is not currently required to send emails using Sinch Mailjet, we still recommend you set it up because it’s just good business. You’ll prevent your domain from getting spoofed and will reduce the chances of fraud causing trouble for your brand. You’ll also improve deliverability.
We also hosted a fireside chat with Yahoo’s Senior Director of Product, Marcel Becker, Google’s Director of Product Anti-Abuse and Safety, Anu Yamunan, and Sinch Mailgun’s Vice President of Deliverability, Kate Nowrouzi, to go through what these new changes mean for email senders. You can watch the full version below:
With DMARC, an organization can prevent malware and phishing attacks, and improve its deliverability all at the same time.
Email deliverability is where email marketing begins. If you want to maximize ROI and engagement while ensuring good customer service, you want the highest possible deliverability rates. To get that, you will want a DMARC record in place.
Once enabled, a DMARC record ensures that only authorized senders are able to use your domain to send emails. That means you can be confident that every email landing in inboxes from your domain really is from your domain.
Short on time and don’t have time to read the whole article? Don’t worry, we’ve got you covered.
The DMARC email authentication protocol can prevent malware and phishing attacks and improve your deliverability all at the same time. Once enabled, DMARC ensures that only authorized senders can use your domain to send emails. That means you can be confident that every email landing in inboxes from your domain really is from your domain.
DMARC has become even more relevant following Gmail and Yahoo announcement of new sending requirements that will affect the whole email marketing world. Failure to comply with these updates could have serious consequences for your organization, so this is not a can to be kicked down the proverbial road.
The good news is these are relatively easy fixes. Here are three changes you need to make:
_dmarc.example.org TXT "v=DMARC1; p=none"We know that for many email senders this is a technically complex topic. That’s why at Sinch Mailjet we’re ready to help. If at any point during the compliance process you have questions, doubts, or just need a little reassurance – our support team is on hand!